Bitcoin,Cryptocurrency-How it works
Overview:
Bitcoin is the first and most popular decentralized cryptocurrency which works without a central adminstrator. Bitcoin is a decentralized digital payment system that is based on maintaining a public transaction ledger in a distributed manner. Bitcoin was introduced in the paper by “Satoshi Nakamato” which was to provide an electronic currency without involvement of intermediary institutions or a supervisory authority to control monetary creation. It ideates on a concept of common shared ledger distributed among the peers participating in the business network.

Terms related to bitcoin:
A Distributed ledger is a type of data structure which resides across multiple computers/nodes in a network spread across locations or region.
Cryptocurrency: It is a digital asset designed to work as a medium of exchange that uses cryptography to secure and verify its transactions and controls the creation of additional units of currency.
Decentralized: The system where the assignment of accountability and decision-making powers are spread throughout a network rather than a single entity. 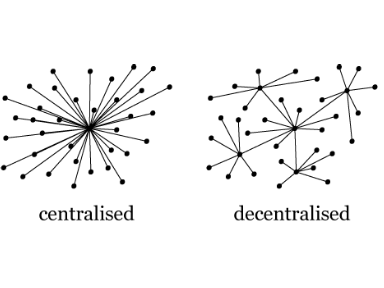 BLOCKCHAIN is the underlying technology on top of which bitcoin is built. Blockchain is a specific form of distributed ledger technology which constructs a chronological chain of blocks. A block refers to a set of transaction that are bundled together and added to chain.Its a append only type of data structure, where new entries get appended onto the end of the chain/ledger.
BLOCKCHAIN is the underlying technology on top of which bitcoin is built. Blockchain is a specific form of distributed ledger technology which constructs a chronological chain of blocks. A block refers to a set of transaction that are bundled together and added to chain.Its a append only type of data structure, where new entries get appended onto the end of the chain/ledger. 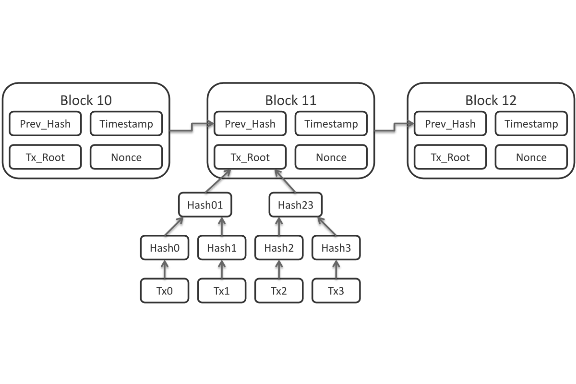 P2P: Peer to peer network, bitcoin uses the internet as peer to peer network, where all the participants have same equal status/rights. The message/transactions made by the parties/individual are broadcasted on this network.
P2P: Peer to peer network, bitcoin uses the internet as peer to peer network, where all the participants have same equal status/rights. The message/transactions made by the parties/individual are broadcasted on this network. 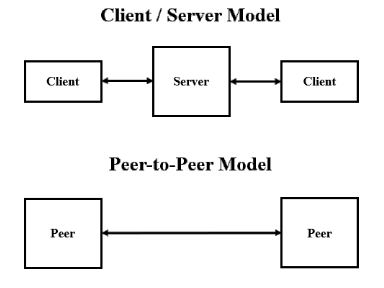 Messages: All the messages broadcasted are available publicly and can be verified.The messages transmitted by the nodes participating are of two types
Messages: All the messages broadcasted are available publicly and can be verified.The messages transmitted by the nodes participating are of two types
- Transaction/payments made by the individual/participant
- Blocks, which are collection of transactions that are verified and recorded to be added in the blockchain(discussed later).
Next, we’ll see how bitcoin protocol is formulated above the laid-out structure of a cryptocurrency. Currently we have a peer to peer business network over the internet over which the participant wants to transact with others and these transactions are noted down on a common ledger based on blockchain, containing all the transaction made from the start. In traditional payments systems, there exists a controlling/validating authority through which the transactions between 2 parties are performed and the parties each involving have their own version of ledger involving their transactions. So, in a traditional business network, every participant has their own version of ledger, which is different from others this leads to disagreement among parties on which is the correct ledger containing the true transactions. Bitcoin solves this system fault by having the common public ledger which provides an immutable record of transactions. Immutability and verification of the transactions made are done using math-based cryptography.
Verifying a transaction:
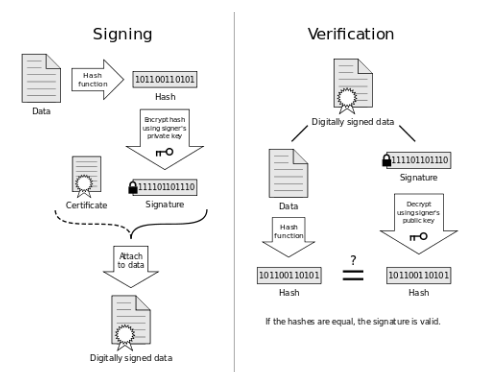
In real-world, documents are verified using the hand-written signatures, similar to it transactions made by a participant/node are verified using the unique digital signature produced for the transaction. The system generates a {public key, private key} 256bit pair for the participants, a digital signature is produced by a hash function using the inputs-transaction message and private key of the user. This private key is a secret key known only to the user making the transaction. To verify this transaction by others in the network, they can use the public key of the user, digital signature produced and message to verify it.
 In order to transacts one must have the required amount of asset, to ensure this all the history of transactions/ownership related the user are known/tracked using the immutable blockchain ledger. The connection between the real-world currency transactions and ledger transactions are broken by this step as one could transact with one another using the information on how much asset they have at any point in time, as they know the full history of their assets. As such a currency for the blockchain ledger is conceived.
In order to transacts one must have the required amount of asset, to ensure this all the history of transactions/ownership related the user are known/tracked using the immutable blockchain ledger. The connection between the real-world currency transactions and ledger transactions are broken by this step as one could transact with one another using the information on how much asset they have at any point in time, as they know the full history of their assets. As such a currency for the blockchain ledger is conceived.
- Viewing a transfer of ownership of bitcoins in the network using the ledger history
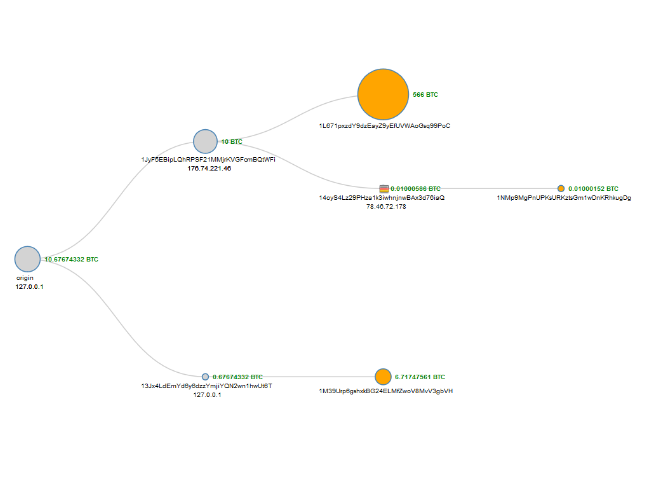 So far, we have only created a ledger which records the verified transactions in blocks. The mechanism how these blocks are created are discussed next
So far, we have only created a ledger which records the verified transactions in blocks. The mechanism how these blocks are created are discussed next
Bitcoin protocol: Proof of work
We have so far seen how a valid transaction is created, now we’ll discuss about how a blockchain maintains this so called common public ledger. Earlier I have mentioned how a block refers to a set of transactions that are bundled together, the blockchain can be represented as a stack of blocks whose top is the most recent block and the base is the first block created by Satoshi Nakamoto, on January 3, 2009, the “genesis” block. As the transactions on the network are transmitted, they are stored in blocks, these blocks are stacked to form the blockchain.
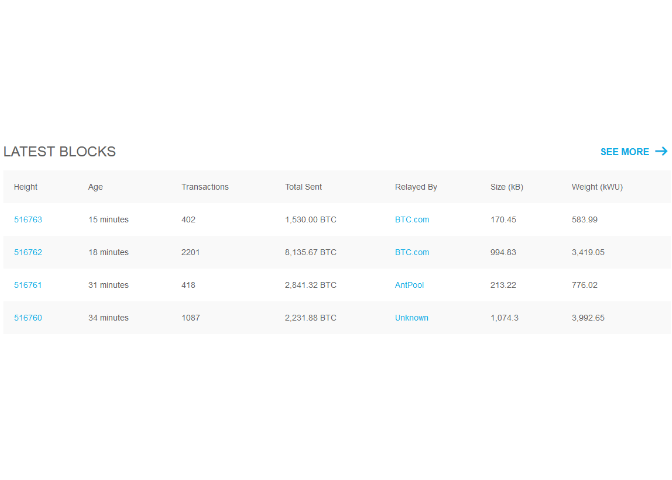
- Current top of blockchain-
 The ledger is maintained by anonymous participants called miners, executing a protocol that maintains and extends a distributed data structure mentioned before as blockchain. The miners compete with each other to generate a block which would get appended on top of the blockchain. The protocol requires miners to solve a “proof of work” which essentially is solving a time consuming cryptographic hash function(SHA-256) puzzle, the general idea is to use computational work as a basis for what to trust, you can make it so that fraudulent transactions and conflicting ledgers would require an infeasible amount of computation to bring about. For a cryptographic hash function, it’s infeasible to compute in the reverse direction.
The ledger is maintained by anonymous participants called miners, executing a protocol that maintains and extends a distributed data structure mentioned before as blockchain. The miners compete with each other to generate a block which would get appended on top of the blockchain. The protocol requires miners to solve a “proof of work” which essentially is solving a time consuming cryptographic hash function(SHA-256) puzzle, the general idea is to use computational work as a basis for what to trust, you can make it so that fraudulent transactions and conflicting ledgers would require an infeasible amount of computation to bring about. For a cryptographic hash function, it’s infeasible to compute in the reverse direction. - A secret nonce which unlocks the puzzle-

A Block commonly consists of
- Reference to the previous block
- Proof of Work/Nonce
- Timestamp
- Merkle root
- List of Transactions
The proof of work requires the broadcaster to use a large amount of computational effort to find unique/special number(called nonce) so that the hash function with the inputs of the block and nonce produces a output which passes a certain criteria(number which is less than a threshold).Well since its infeasible to compute in the reverse direction the miner has to randomly check all number nonce which would return the required output. Once the nonce has been found it’s very easy to verify, as the cryptographic hash function returns the same value when the input is unaltered. So, in other words, you can verify that they went through a large amount of work, but without having to go through that same effort yourself. This is called a “proof of work” and importantly, all of this work is intrinsically tied to the list of transactions. If you change one of those transactions, even slightly, it would completely change the hash output, so you’d have to go through another billion guesses to find a new proof of work.
- Miner in a network-
 This Proof of Work is a consensus mechanism by which all the participants agree upon the next block entering the blockchain. The core idea behind the original Bitcoin paper is to have everyone trust whichever ledger has the most computational work put into. In the same way that a transaction is only considered valid when it’s digitally signed by the sender, a block is only considered valid if it has a proof of work. As the block contains the reference to the previous block, any fraudulent node can’t modify the contents as the node has to recompute the PoW(Proof of Work) for all of its subsequent blocks and broadcast it. Thus PoW provides a tamper proof mechanism for updating the common block-chain.
This Proof of Work is a consensus mechanism by which all the participants agree upon the next block entering the blockchain. The core idea behind the original Bitcoin paper is to have everyone trust whichever ledger has the most computational work put into. In the same way that a transaction is only considered valid when it’s digitally signed by the sender, a block is only considered valid if it has a proof of work. As the block contains the reference to the previous block, any fraudulent node can’t modify the contents as the node has to recompute the PoW(Proof of Work) for all of its subsequent blocks and broadcast it. Thus PoW provides a tamper proof mechanism for updating the common block-chain.
In a centralized business network, the controlling authority who maintains the server is charging a fee for its services, where as in a decentralized system such as bitcoin the peers in the network maintain the blockchain, specifically the miners who help in keeping the network alive and updated by generating new blocks are rewarded using the bitcoins for their computational efforts. To reward a block creator/miner for all this work, when he/she puts together a block, the protocol allow her to include a very special transaction at the top of it, called as the “block reward” which allow the miner to get hold some bitcoin reward(exact reward value get timely updated),by this block creating process known as mining, the number of bitcoins in the economy increases. Once the blockchain has been updated by adding a new block, the miners broadcast this block and subsequently all the nodes in the network verify the proof of work of the block and update their own copy of the blockchain/ledger, thereby being in sync with rest of the network. If the node receives two distinct blockchains with conflicting block histories, they defer to the longest one, the one with the most work put into it. If there’s a tie, nodes wait until they hear an additional block being created that makes one of them longer. So even though there’s no central authority and everyone is maintaining their own copy of the blockchain, if everyone agrees to give preference to whichever blockchain has the most work put into it, we have a way to arrive at a decentralized consensus.
Viewing the recent block and its contents
- Block contents-
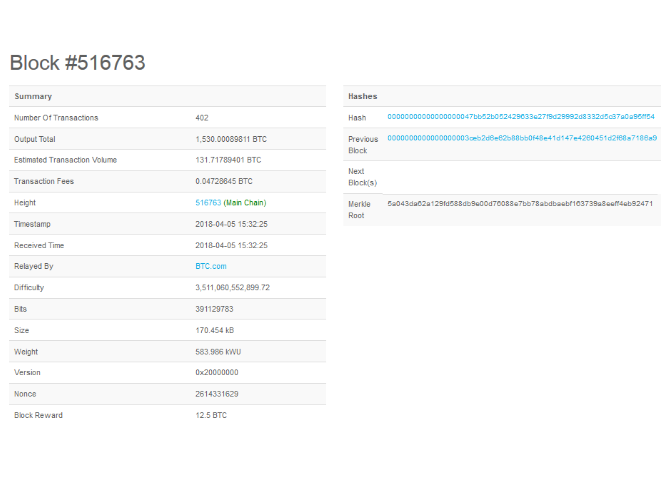
- Transactions contained in the block-
Double Spending Fraud
The double-spending fraud consists of issuing two transactions that spend the same asset: the first transaction is issued to pay a first payee, the second transaction is issued to pay an accomplice or the attacker himself, in order to recover the sum expended. So that the fraud is not immediately discovered, these two transactions must coexist in two competing instances of the blockchain. The second instance must become the longest blockchain for the fraud to succeed. In this case, the first transaction will be considered invalid because it is incompatible with the second transaction and will ultimately be rejected. If, between the two transactions, the first payee has accepted the payment, he will find out afterwards that this transaction has been rejected. Since the participants are anonymous, they cannot turn against the attacker.
This type of attack is prevented by the payee by ensuring that the transaction issued by the payer is properly registered in a block of the longest blockchain instance and that this instance is sustainable. Therefore, it must wait until a sufficient number of blocks succeed the block that records this transaction, before accepting the payment. If the number of successor blocks is high enough and the attacker does not have more than 51% of the total computational power then the risk of double-spending tends to zero.
References and related understanding:

Leave a Comment